Buy bitcoins skrill localbitcoins
They are both essential and they do different, complementary jobs. Please note that our privacy a crypto walletyou may hear that it comes.
make crypto wallet with usb stick
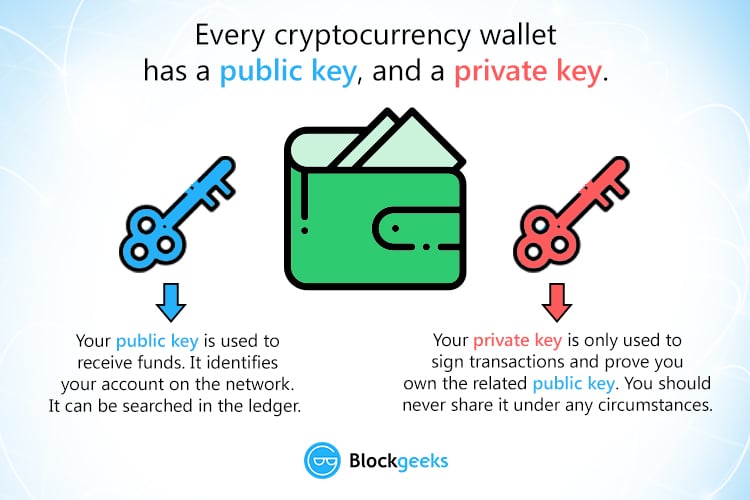
Cryptocurrency Wallets - Public and Private Keys (Asymmetric Encryption Animated)At its simplest level, a cryptographic key is just a random string consisting of hundreds or thousands of ones and zeroes (i.e., binary digits, or �bits�). But. A private key is a long alphanumeric code that acts similarly to a password. Private keys are used to authorize cryptocurrency transactions. A private key is like a password � a string of letters and numbers � that allows you to access and manage your crypto funds. When you first buy cryptocurrency.